Overview:
MS355-24X Highlights
Switch ports/stacking ports
- 8 × mGig ports
- 16 × 1G ports
- 2 × 40G or 4 × 10G fiber uplinks
- Stack up to 8 units
- QSFP28 stacking ports
Power/PoE
- All models include 740W
- Up to 30W per 1G port
- Up to 60W per mGig port
- Modular power supply/fans
Hardware platform
- Reliable platform with 24/7 Meraki Support
- Clean lines and beautiful design
- Voice and video QoS
- Non-blocking switch fabric
Cloud management
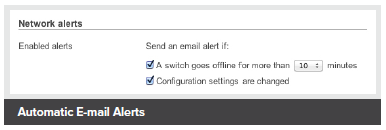
- Email alerts for switch management
- Remote troubleshooting tools
- Manage ports from a GUI-based dashboard
- Zero-touch provisioning
- Per-port and per-client usage statistics
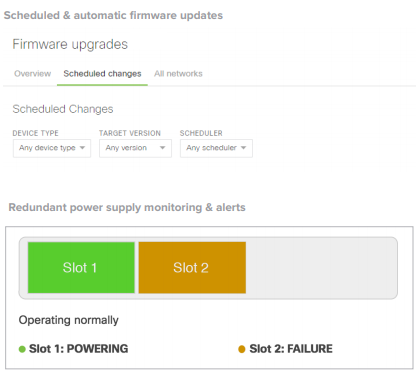
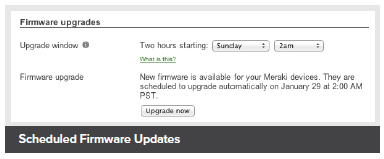
- Secure, user-scheduled firmware updates
Switching capabilities
- Layer 3
- Warm spare redundancy (VRRP)
- OSPF Routing
- MAC forwarding entries, up to 32K
- DHCP Server, DHCP Relay
- 802.1X Authentication
- DHCP Snooping
- STP Enhancements
- IPv4 and IPv6 ACLs
Cloud-Managed Stackable Multi-Gigabit Switches
The Cisco Meraki MS355 series provides full 10G multi-gigabit (mGig) access switching for demanding enterprise and campus environments.
The switch series features a high mGig port density for 802.11ax wireless access points, servers, and workstations. The family supports 40G or 10G uplinks, physical stacking, up to 60W of port power with UPoE, and field replaceable power supplies/fans.
All Meraki switches are managed through an elegant, intuitive cloud-based interface, rather than cryptic command line. To bring up a Meraki switch, simply plug it in. Meraki switches do not require CLI for switch configuration or port management. Meraki’s centralized management platform gives administrators granular visibility into their network. Our dashboard helps you keep track of every configuration change in your network with our detailed event and change logs.
 Industry Leading Cloud Management
Industry Leading Cloud Management
Cloud management has many benefits that make it easier to build networks large and small:
- Automatic email alerts from power loss, downtime, excessive Layer 1 errors, or configuration changes
- Powerful remote diagnostic tools such as packet capture to help isolate and troubleshoot network issues
- Role-based administration
- Firmware upgrades and enhancements from the Meraki cloud
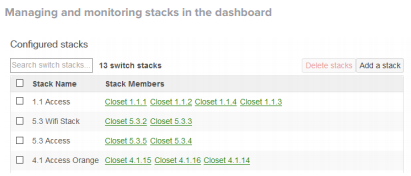
- Virtual Stacking enables switch port configuration changes on the dashboard interface without the need to physically stack switches
- Incredible network transparency with application, operating system, client, and hostname visibility
- Zero-touch provisioning for rapid deployment across sites
Features and Capabilities:
Powerful Access Switching
- High-bandwidth physical stacking with support for up to 8 stack members for built-in redundancy and performance
- Link Aggregation Control Protocol (LACP) for high-capacity trunking, with Multichassis (MLAG) support on stacked switches
- Static and dynamic routing support with DHCP relay and server capabilities
- Quality-of-Service (QoS) to prioritize mission-critical traffic such as voice and video
- Voice VLAN support for simplified VoIP deployments
- CDP, LLDP advertisement and snooping, with detailed neighbor visibility and discovery
- Port Mirroring to monitor network traffic
- IGMP Snooping to optimize network performance for multicast applications
Network Security
- IEEE 802.1X, MAB, and Hybrid authentication support for wired access control with RADIUS server monitoring
- ACL support (IPv4 & IPv6) and MAC whitelisting
- Single-Host/Multi-Domain/Multi-Host/Multi Authentication
- Change of Authorization (CoA) and RADIUS accounting support
- DHCP snooping to protect against rogue DHCP servers on the network
- Dynamic ARP Inspection to prevent man-in-the-middle attacks
- Rapid Spanning Tree, BPDU guard, root guard, loop guard, and other safeguards to help prevent misconfigurations and reduce convergence time
- Per port VLAN configuration
- Multiple administrative roles with sophisticated security policy management
Network Troubleshooting & Automation
- Virtual Stacking helps IT admins make configuration changes to hundreds of switch ports in seconds with our intuitive dashboard interface
- Configuration templates for rapid, zero-touch provisioning and auditing of all sites
- Network Topology for automatic and interactive network mapping
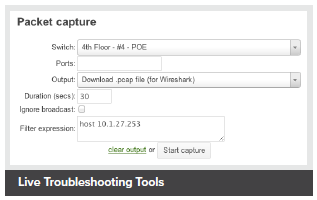
- Remote cable testing, packet capture, and client discovery
- Automatic and scheduled firmware upgrades for the complete network
Converged Voice, Video and Data Environments
The Meraki switch family is designed to unify data, voice, and video onto a single IP backbone. All Meraki switches support rich qualityof-service (QoS) functionality for prioritizing data, voice, and video traffic. The switches support eight class-of-service (CoS) queues on every port, enabling them to maintain end-to-end traffic prioritization.
PoE models provide power to VoIP telephones, IP security cameras, wireless access points (APs), and other IP devices. Using CDP and LLDP, PoE power is intelligently budgeted to maximize the number of PoE clients supported. For the most power-hungry applications, support for UPoE support is also available.
Application Layer Visibility
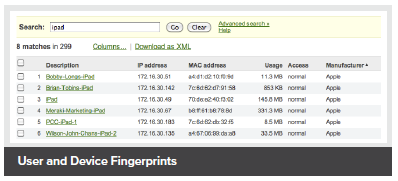
Meraki switches include integrated Layer 7 fingerprinting without the need to purchase additional modules or services. Identify hundreds of applications from business apps to BitTorrent and YouTube.
User fingerprinting allows administrators to quickly identify individual users by device and tune network resources for optimum performance.
Beyond the Network Software Architecture
Meraki switches run the same operating system used by all of our products, which allows us to deliver a consistent user experience for network management.
When connected, new MS355 switches automatically reach out to the Meraki cloud and download the most current configuration. Future updates can be user-scheduled, ensuring the network is kept up-to-date with bug fixes, security updates, and new features.
Cloud Management:
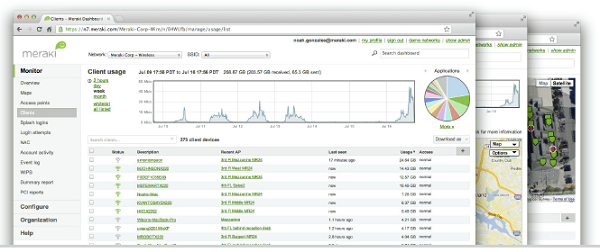
Cisco Meraki's cloud based management provides centralized visibility & control over Cisco Meraki's wired & wireless networking hardware, without the cost and complexity of wireless controllers or overlay management systems. Integrated with Cisco Meraki's entire product portfolio, cloud management provides feature rich, scalable, and intuitive centralized management for networks of any size.
Highlights
- Unified visibility and control of the entire network via a single dashboard: wireless, switching, and security appliances
- Streamlines large networks with tens of thousands of endpoints
- Zero-touch provisioning for rapid deployment
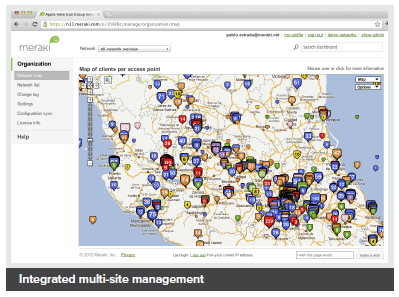
- Built-in multi site network management tools
- Automated network monitoring and alerts
- Intuitive interface eliminates costly training or added staff
- Network tagging engine - search and sync settings by tag
- Role-based administration and auditable change logs
- Continuous feature updates delivered from the cloud
- Highly available and secure (PCI / HIPAA compliant)
Cloud Managed Networks
Cisco Meraki's hardware products are built from the ground up for cloud management. As a result, they come out of the box with centralized control, layer 7 device and application visibility, real time web-based diagnostics, monitoring, reporting, and much more.
Cisco Meraki networks deploy quickly and easily, without training or dedicated staff. Moreover, Cisco Meraki provides a rich feature set that provides complete control over devices, users, and applications, allowing for flexible access policies and rich security without added cost or complexity.
Cisco Meraki's cloud management provides the features, security, and scalability for networks of any size. Cisco Meraki scales from small sites to campuses, and even distributed networks with thousands of sites. Cisco Meraki devices, which self-provision via the cloud, can be deployed in branches without IT. Firmware and security signature updates are delivered seamlessly, over the web. With the cloud, branches can automatically establish secure VPN tunnels between one another with a single click.
With a secure, PCI and HIPAA compliant architecture and fault tolerant design that preserves local network functionality during WAN outages, Cisco Meraki is field proven in high security and mission critical network applications.
Cloud Management Architecture
Cisco Meraki's architecture provides feature rich network management without on-site management appliances or WiFi controllers.
Every Cisco Meraki device - including wirelesss access points, Ethernet switches, and security appliances - connects over the Internet to Cisco Meraki's datacenters, which run Cisco Meraki's cloud management platform. These connections, secured via SSL, utilize a patented protocol that provides real time visibility and control, yet uses minimal bandwidth overhead (typically 1 kbps or less.)
In place of traditional command-line based network configuration, Cisco Meraki provides a rich web based dashboard, providing visibility and control over up to tens of thousands of Cisco Meraki devices, anywhere in the world. Tools, designed to scale to large and distributed networks, make policy changes, firmware updates, deploying new branches, etc. simple and expedient, regardless of size or location. Cisco Meraki's real time protocols combine the immediacy of on-premise management applications with the simplicity and centralized control of a cloud application.
Every Cisco Meraki device is engineered for cloud management. Specifically, this means that Cisco Meraki devices are designed with memory and CPU resources to perform packet processing, QoS, layer 3-7 security, encryption, etc. at the network edge. As a result, no network traffic passes through the cloud, with the cloud providing management functionality out of the data path. This architecture enables networks to scale horizontally, adding capacity simply by adding more endpoints, without concern for centralized bottlenecks or chokepoints. Equally important, since all packet processing is performed on premise, end-user functionality is not compromised if the network's connection to the cloud is interrupted.
Cisco Meraki's cloud platform is designed to spread computation and storage across independent server clusters in geographically isolated datacenters. Any server or datacenter can fail without affecting customers or the rest of the system. Additionally, Cisco Meraki's datacenter design is field proven to support tens of thousands of endpoints.
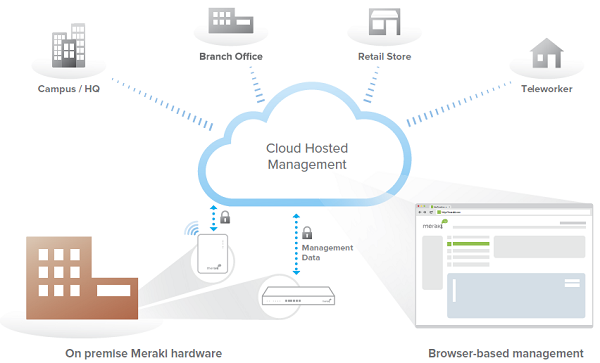
Cloud Management Architecture
Powerful Insight and Troubleshooting Tools
Cisco Meraki's cloud architecture delivers powerful insight and includes live tools integrated directly into the dashboard, giving instant analysis of performance, connectivity, and more. Using live tools, network administrators no longer need to go on site to perform routine troubleshooting tests. Visibility into devices, users, and applications gives administrators the information needed to enforce security policies and enable the performance needed in today's demanding network environments.
Troubleshooting tools such as ping, traceroute, throughput, and even live packet captures are integrated directly into the Cisco Meraki dashboard, dramatically reducing resolution times and enabling troubleshooting at remote locations without on-site IT staff.
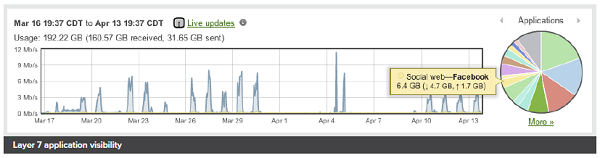
Layer 7 application visibility
Out-of-Band Control Plane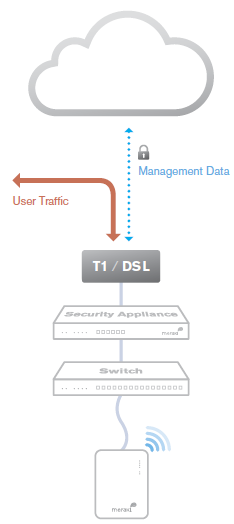
Cisco Meraki's out-of-band control plane separates network management data from user data. Management data (e.g., configuration, statistics, monitoring, etc.) flows from Cisco Meraki devices (wireless access points, switches, and security appliances) to Cisco Meraki's cloud over a secure Internet connection. User data (web browsing, internal applications, etc.) does not flow through the cloud, instead flowing directly to its destination on the LAN or across the WAN.
Advantages of an out of band control plane:
Scalability
- Unlimited throughput: no centralized controller bottlenecks
- Add devices or sites without MPLS tunnels
- Add switching capacity without stacking limitations
Reliability
- Redundant cloud service provides high availability
- Network functions even if management traffic is interrupted
Security
- No user traffic passes through Cisco Meraki's datacenters
- Fully HIPAA / PCI compliant
What happens if a network loses connectivity to the Cisco Meraki cloud?
Because of Cisco Meraki's out of band architecture, most end users are not affected if Cisco Meraki wireless APs, switches, or security appliances cannot communicate with Cisco Meraki's cloud services (e.g., because of a temporary WAN failure):
- Users can access the local network (printers, file shares, etc.)
- If WAN connectivity is available, users can access the Internet
- Network policies (firewall rules, QoS, etc.) continue to be enforced
- Users can authenticate via 802.1X/RADIUS and can roam wirelessly between access points
- Users can initiate and renew DHCP leases
- Established VPN tunnels continue to operate
- Local configuration tools are available (e.g., device IP configuration)
While Cisco Meraki's cloud is unreachable, management, monitoring, and hosted services are temporarily unavailable:
- Configuration and diagnostic tools are unavailable
- Usage statistics are stored locally until the connection to the cloud is re-established, at which time they are pushed to the cloud
- Splash pages and related functionality are unavailable
Cisco Meraki Datacenter Design
Cisco Meraki's cloud management service is colocated in tier-1, SAS70 type II certified datacenters. These datacenters feature state of the art physical and cyber security and highly reliable designs. All Cisco Meraki services are replicated across multiple independent datacenters, so that customer-facing services fail over rapidly in the event of a catastrophic datacenter failure.
Redundancy
- Five geographically dispersed datacenters
- Every customer's data (network configuration and usage metrics) replicated across three independent datacenters
- Real-time data replication between datacenters (within 60 seconds)
- Nightly archival backups
Availability Monitoring
- 24x7 automated failure detection — all servers are tested every five minutes from multiple locations
- Rapid escalation procedures across multiple operations teams
- Independent outage alert system with 3x redundancy
Disaster Recovery
- Rapid failover to hot spare in event of hardware failure or natural disaster
- Out of band architecture preserves end-user network functionality, even if connectivity to Cisco Meraki's cloud services is interrupted
- Failover procedures drilled weekly
Cloud Services Security
- 24x7 automated intrusion detection
- Protected via IP and port-based firewalls
- Access restricted by IP address and verified by public key (RSA)
- Systems are not accessible via password access
- Administrators automatically alerted on configuration changes
Physical Security
- High security card keys and biometric readers control facility access
- All entries, exits, and cabinets are monitored by video surveillance
- Security guards monitor all traffic into and out of the datacenters 24x7, ensuring that entry processes are followed
Out-of-Band Architecture
- Only configuration and usage statistics are stored in the cloud
- End user data does not traverse through the datacenter
- All sensitive data (e.g., passwords) stored in encrypted format
Disaster Preparedness
- Datacenters feature sophisticated sprinkler systems with interlocks to prevent accidental water discharge
- Diesel generators provide backup power in the event of power loss
- UPS systems condition power and ensure orderly shutdown in the event of a full power outage
- Each datacenter has service from at least two top-tier carriers
- Seismic bracing for raised floor, cabinets, and support systems
- In the event of a catastrophic datacenter failure, services fail over to another geographically separate datacenter
Environmental Controls
- Over-provisioned HVAC systems provide cooling and humidity control
- Flooring systems are dedicated for air distribution
Certification
- Cisco Meraki datacenters are SAS70 type II certified
- PCI level 1 certified
Service Level Agreement
- Cisco Meraki's cloud management is backed by a 99.99% uptime SLA. See www.Cisco Meraki.com/trust for details.
Security Tools for Administrators
In addition to Cisco Meraki's secure out-of-band architecture and hardened datacenters, Cisco Meraki provides a number of tools for administrators to maximize the security of their network deployments. These tools provide optimal protection, visibility, and control over your Cisco Meraki network.
Two-factor authentication
Two-factor authentication adds an extra layer of security to an organization's network by requiring access to an administrator's phone, in addition to her username and password, in order to log in to Cisco Meraki's cloud services. Cisco Meraki's two factor authentication implementation uses secure, convenient, and cost effective SMS technology: after entering their username and password, an administrator is sent an a one-time passcode via SMS, which they must enter before authentication is complete. In the event that a hacker guesses or learns an administrator's password, she still will not be able to access the organization's account, as the hacker does not have the administrator's phone. Cisco Meraki includes two-factor authentication for all enterprise users at no additional cost.
Password policies
Organization-wide security policies for Cisco Meraki accounts help protect access to the Cisco Meraki dashboard. These tools allow administrators to:
- Force periodic password changes (e.g., every 90 days)
- Require minimum password length and complexity
- Lock users out after repeated failed login attempts
- Disallow password reuse
- Restrict logins by IP address
Role-based administration
Role-based administration lets supervisors appoint administrators for specific subsets of an organization, and specify whether they have read-only access to reports and troubleshooting tools, administer managed guest access, or can make configuration changes to the network. This minimizes the chance of accidental or malicious misconfiguration, and restricts errors to isolated parts of the network.
Configuration change alerts
The Cisco Meraki system can automatically send human-readable email and text message alerts when configuration changes are made, enabling the entire IT organization to stay abreast of new policies. Change alerts are particularly important with large or distributed IT organizations.
Configuration and login audits
Cisco Meraki logs the time, IP, and approximate location (city, state) of logged in administrators. A searchable configuration change log indicates what configuration changes were made, who they were made by, and which part of the organization the change occurred in.
SSL certificates
Cisco Meraki accounts can only be accessed via https, ensuring that all communication between an administrator's browser and Cisco Meraki's cloud services is encrypted.
Idle Timeout
30 seconds before being logged out, users are shown a notice that allows them to extend their session. Once time expires, users are asked to log in again.


 Industry Leading Cloud Management
Industry Leading Cloud Management